In today's digital age, cyber threats are evolving at an alarming rate, posing significant risks to businesses, governments, and individuals. Cybercriminals are leveraging advanced technologies to launch sophisticated attacks, making it crucial for organizations to stay informed and prepared. From AI-powered phishing schemes to large-scale ransomware attacks, the cybersecurity landscape is more dangerous than ever. Understanding the latest threats and implementing proactive security measures can help mitigate risks and protect sensitive data.
1. AI-Powered Phishing Attacks
Phishing remains one of the most prevalent cyber threats, but recent advancements in artificial intelligence have made these attacks more sophisticated. Cybercriminals now use AI-driven algorithms to craft highly convincing phishing emails, mimicking legitimate sources with near-perfect accuracy. These emails often include personalized details, making it harder for users to identify them as fraudulent. Additionally, deepfake technology is being utilized to manipulate audio and video, allowing hackers to impersonate executives or trusted individuals to trick employees into divulging sensitive information.
2. Ransomware Attacks on Critical Infrastructure
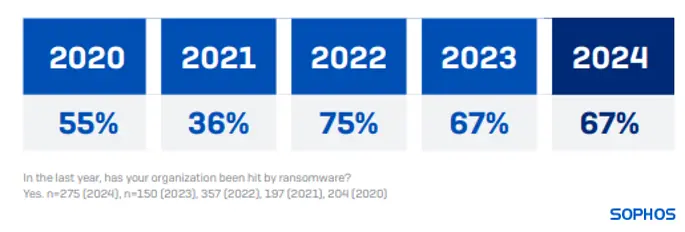
Ransomware attacks continue to rise, with cybercriminals increasingly targeting critical infrastructure such as healthcare facilities, energy providers, and government institutions. Attackers use advanced encryption techniques to lock users out of their systems, demanding hefty ransom payments in exchange for restoring access. High-profile incidents like the Colonial Pipeline attack highlight the devastating impact of these breaches, disrupting essential services and causing financial losses. Organizations must prioritize cybersecurity measures, including regular data backups, employee training, and the deployment of advanced threat detection solutions.
3. Supply Chain Attacks
Supply chain attacks have become a significant concern as hackers infiltrate software providers to gain access to a wide range of users. In these attacks, cybercriminals compromise trusted software vendors and insert malicious code into their products, affecting thousands of organizations worldwide. The SolarWinds and Kaseya breaches serve as prime examples of how attackers can exploit supply chain vulnerabilities. To combat this threat, businesses must conduct rigorous security audits of their vendors and implement zero-trust security models to verify the integrity of all software updates.

4. Zero-Day Exploits and Advanced Persistent Threats (APTs)
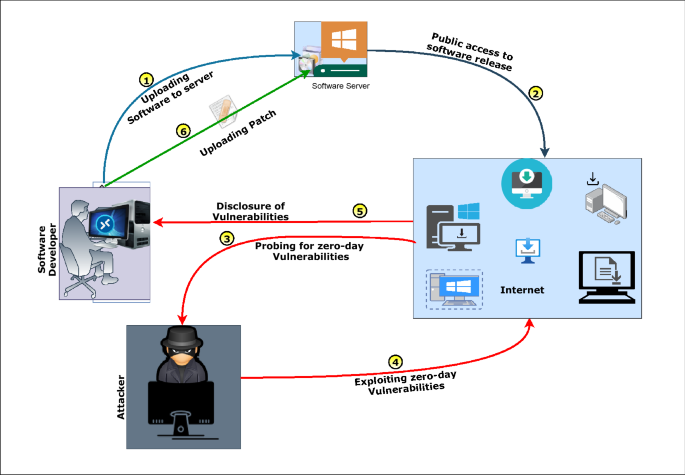
Zero-day vulnerabilities, which are security flaws unknown to software vendors, pose significant risks to organizations. Cybercriminals actively seek out and exploit these vulnerabilities before patches are available, allowing them to infiltrate systems undetected. Additionally, Advanced Persistent Threats (APTs) involve prolonged, stealthy cyberattacks conducted by well-funded threat actors, often linked to nation-states. These attackers infiltrate networks and remain undetected for extended periods, gathering intelligence or causing damage. Regular system updates, robust endpoint protection, and continuous network monitoring are essential to defend against these threats.
Conclusion
The ever-evolving cybersecurity landscape demands constant vigilance and proactive security measures. Organizations and individuals must stay informed about the latest cyber threats and adopt comprehensive security strategies to mitigate risks. Implementing multi-layered security solutions, conducting regular security assessments, and fostering a culture of cybersecurity awareness can help protect against emerging threats. As cybercriminals continue to refine their tactics, staying one step ahead with robust cybersecurity defenses is the key to safeguarding digital assets and sensitive information.





